Let’s face it—when you’re working in the cloud, security isn’t optional. It becomes even more important on public cloud platforms like AWS. Out of the six pillars in the AWS Well-Architected Framework, security stands out as the one you really can’t afford to ignore.
Now, AWS gives you a few ways to build—think SaaS, PaaS, and IaaS. In this case, we focused on the IaaS model. That’s where Amazon EC2 comes in—basically, virtual machines that let you run apps and workloads in the cloud.
We suggested this route to our customer, and they ran with it. The result? A much stronger security setup tailored for their AWS environment.
Why Systems Manager (SSM) Replaces SSH for Connecting to EC2 Instances
For a long time, SSH was the default way to connect securely to EC2 instances. It worked—but it came with baggage. Managing SSH key pairs can be tricky, and if someone mishandles them, that’s a real security risk. Plus, using SSH means you have to open up port 22 on your instance, which invites inbound traffic from the internet. Not ideal.
That’s where AWS Systems Manager (SSM) Session Manager comes in—and honestly, it’s a smarter alternative. No need for key pairs. No open ports. No extra exposure. With SSM, you get a secure, logged connection to your EC2 instances—without putting them out there on the internet.
Even better, it plays nicely with AWS IAM, so you can control who gets access and keep things tight and traceable. You can handle your instances right from the AWS Console or CLI, and all sessions are encrypted by default.
In short: fewer risks, more control, and a smoother way to manage your EC2s.
Enhancing EC2 Session Manager with KMS Encryption
If you—or your customer—are working inside an AWS account, how you connect to EC2 instances really matters. There are a few ways to do it, but AWS Systems Manager (SSM) Session Manager stands out. It lets you securely access your instances without juggling SSH keys or tweaking security group rules to open up ports. No exposed surfaces, no extra fuss.
To make it work, there are just a few boxes to tick: the SSM Agent needs to be installed and running, the instance should be able to reach Systems Manager endpoints, and IAM roles and permissions must be set up right.
Once that’s in place, you’re good to go. You can connect straight from the AWS Console using Session Manager. The connection is encrypted by default using AWS-managed keys and TLS 1.2—so security is baked in.
Need an extra layer for sensitive data or compliance-heavy environments? You can bring in AWS Key Management Service (KMS) to encrypt those sessions with your own keys. That way, you stay in control of key usage and audits.
Two Approaches for Session Encryption with KMS
1. Standalone KMS Key (Single Account Setup)
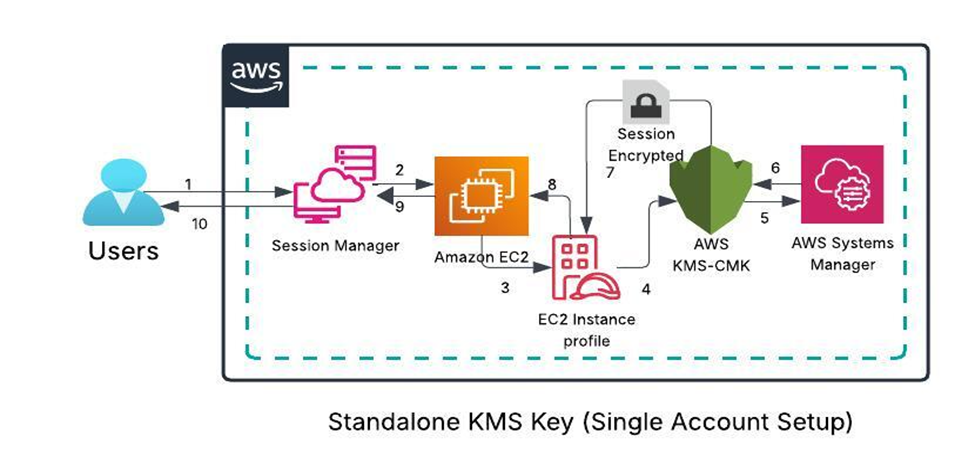
If you’re operating within a single AWS account, follow these steps:
- Create a KMS key in your account.
- Update the key policy to allow only the Systems Manager service to use this key and assign a dedicated IAM role to manage the key.
- In Session Manager preferences, enable session encryption and specify the newly created KMS key ARN.
- Attach a policy to the EC2 instance profile role that grants decryption permission for the KMS key.
This ensures that all session data is encrypted using your own customer-managed key rather than the default AWS-managed key.
2. Centralized KMS Key (Multi-Account / Organization Setup)
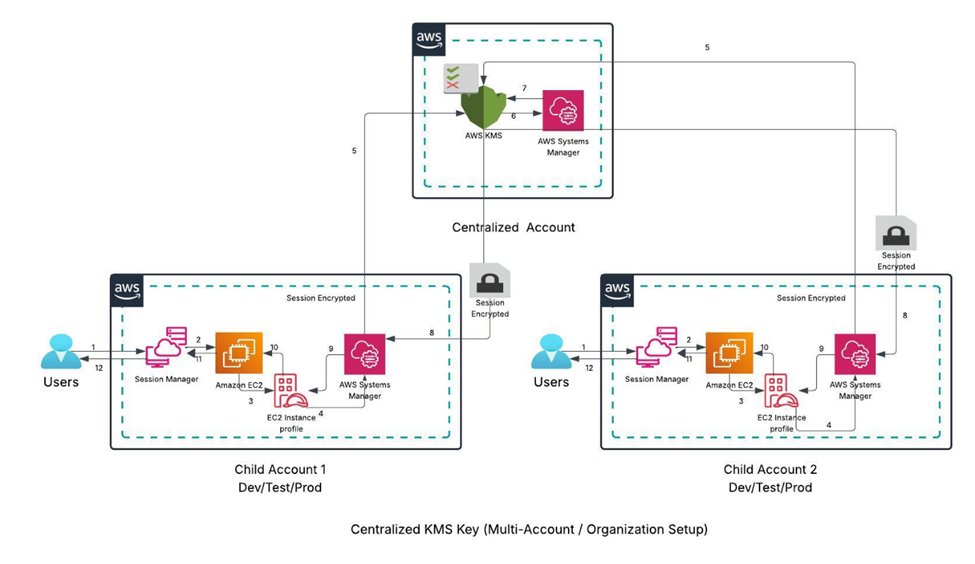
In an AWS Organization setup with multiple accounts:
Create a centralized KMS key in a designated account (e.g., a Security or Shared Services account).
Update the KMS key policy to:
- Allow access to SSM service
- Allow decryption by specific IAM roles in child accounts
- Optionally, use the organization ID to grant access broadly within your org.
In the child accounts, update the EC2 instance role to include permission to use the centralized KMS key.
In Session Manager settings, reference the centralized key ARN.
This centralized approach simplifies key management and improves scalability by eliminating the need for separate keys in each account.
Want to Strengthen Your AWS Security Posture?
At WinWire, we help organizations implement secure, scalable cloud architectures using AWS best practices. Whether you’re just starting out with SSM and KMS or looking to overhaul your entire cloud governance model—we’re here to help.